How to improve the online security of your wedding and event business for free
You most likely have heard on the news countless times about large companies or even public organisations getting hacked.
Sure, you could say “why would a hacker be interested in my humble wedding business?” According to the 2018 Cyber Security Breaches Survey carried by the government, 42% of small or micro-businesses in the UK reported a data breach or cyber attack in the previous 12 months. In 17% of cases, it took businesses a day or more to recover from the breach.
Imagine a breach occurring during peak wedding season and your business was offline for a day or even longer. That spells disaster and could irreversibly damage the reputation of your business that you have worked so hard to build.
There are a lot of procedures you can do such as auditing and risk assessments to prepare for a cyber attack. However, we are going to focus on exploring simple options you can implement today that are free! We will also talk about a few paid solutions towards the end.
DISCLAIMER
The Wedding Insurance Group cannot be held responsible for any cyber breaches or attacks if you decide to use the following options. The purpose of this article is to bring to your attention the issues surrounding online security and explore some solutions. By using these options, you are entirely responsible for the outcomes.
Furthermore, there is no such thing as being fully hacker-proof at the moment. However, there are steps you can take to put up more obstacles. This may decrease the probability of a hacker(s) succeeding by overcoming basic security weaknesses.
Table of contents
1. Use secure passwords with random characters
2. Use a third-party password manager
3. Use different passwords for everything
4. Use two-factor authentication (2FA) where possible
5. Use an alphanumeric password to unlock your phone
6. Use a VPN if you are using public WIFI or avoid it altogether
7. Use anti-virus software and scan regularly
8. Lockdown your social media accounts
9. Google your personal information and remove results
10. Ensure your website is regularly backed up
11. Do not click any links in suspicious emails or messages
12. Use credit cards for online purchases
13. Get cyber and data risks insurance
14. Concluding thoughts
Use secure passwords with random characters
You’ve probably seen prompts when signing up to a website encouraging you to create a strong password. For example, here is a weak password:
weddingbusiness2018
Here is a strong password:
d8’P,K|”bj%7″K<9st6G
Hackers don’t guess passwords; they use computers which are very good at working out password variations at speed. Using actual words and predictable numbers makes this process easier.
Creating a password with a random mixture of upper and lower case letters, numbers and special characters is the best way to increase the difficulty of hacking it. Remember, the longer the password, the better such as:
$5’FgtLX+yz.}K:_{LR!’y|zMTj3HC”?G#;4>}}@
You can use a password generator online. If you really want to increase the chances of no one knowing what combination you have used, type in random keys on a word document offline then copy and paste it across.

It’s unlikely you are going to remember these passwords. Consider using a dedicated password manager before you are tempted to save these passwords in your browser.
Use a third-party password manager
A third party password manager is a tool and mobile app that stores all your passwords securely. Most people store their passwords in their web browsers. The problem is browsers do not use the same level of sophisticated security as a dedicated third-party password manager.
Another problem with storing passwords in your browsers is the autofill feature. Your browser uses this to automatically fill out repetitive form fields such as name, email and passwords. However, this feature can also be used by hackers to steal your information as reported by the Guardian.
There are numerous password managers available online. You can view a comparison table here. Some providers like Dashlane are free who let you store up to 50 passwords. You just have to remember one master password.

Like the others, make your master password strong and random if possible. If you are struggling to remember it, consider writing it down and storing in a safe location offline.
When choosing a third-party password manager, it’s worth noting whether they offer the ability to reset your master password. This could be a vulnerability. Malicious actors may attempt to reset your password using account recovery processes. It’s best to choose a password manager that does not allow master passwords to be reset.
On this note, if you lose or forget your master password, you may have reset your account and start from scratch. In my opinion, this is worth the effort to ensure you are minimising the possibility of someone stealing all of your passwords in one go.
A word of caution though! Most major password managers offer a browser extension which automatically logs into websites of your choice. This is similar to the autofill function on web browsers. These extensions can provide a gateway in for hackers to steal your information.
To use a password manager securely, copy and paste the password over from the desktop or mobile app although this will take more time. If you do decide to use the browser extension, password managers usually offer to keep you logged in for a certain amount of time. It would be best not to use this option. You may wish to log in to your browser extension every time you access the internet.
As with a lot of cybersecurity measures, you have to find a balance between the integrity of your security and personal convenience.
Use different passwords for everything
I’ve been guilty of this one in the past by using the same password across multiple websites such as social media and email. It’s understandable why people use the same password because it’s easier to remember.
If one password falls into the wrong hands, the likelihood of a hacker(s) accessing your other sites increases significantly. But it’s impractical to remember lots of different passwords. That’s another reason why using a password manager makes sense.
Use two-factor authentication (2FA) where possible
Two-factor authentication (2FA) is another layer of identity confirmation. It is also referred to as two-step verification. One of the most common methods we use is chip and PIN. The same principle applies online.
A lot of websites now provide this extra layer of security. You are asked to provide additional information to confirm your identity on top of a password and username or email address.
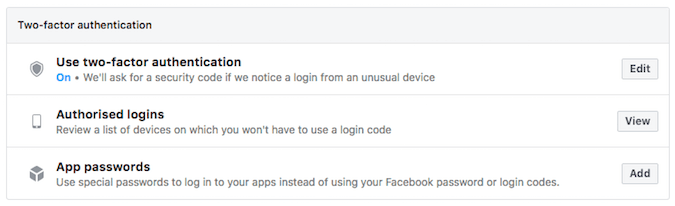
For example, the website may text your phone with a verification code. Another example currently offered by Google involves verifying your identity on a registered mobile device that is signed in to your Google account using their apps.
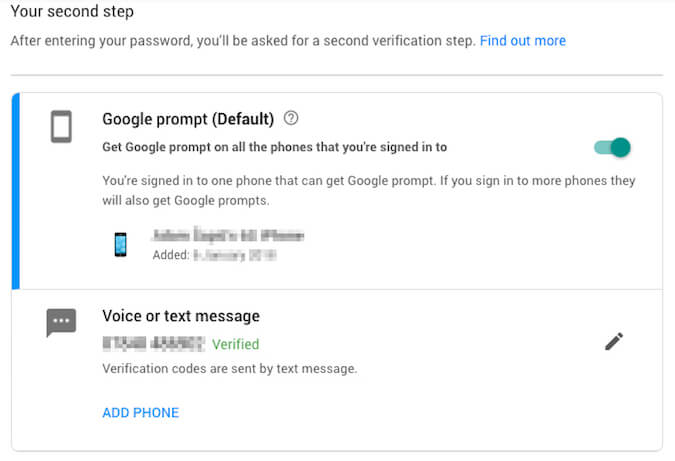
You could even install a security key on a USB device which your computer will require when signing in. Some mobile apps use your fingerprints as the second identity factor.
2FA adds an additional layer of identification and I recommend you activate it where possible. Usually, this process will involve your phone which can be stolen or lost. Many 2FA providers have an option where you can reset information using backup numbers or codes. It’s worth checking this out to make sure you have a plan if things go wrong with your phone.
It’s worth noting certain methods of 2FA such as sending a code to your phone can be intercepted by hackers using call hijacking technology. If you want to find out more about which methods of 2FA are more secure, search online and weigh up your options.

Again, 2FA will increase the amount of time it requires to sign in. Some websites offer the ability for you to ‘save your browser’ or ‘remember your device’ so you don’t have to keep going through the authentication process.
Again, this option of convenience could be a gateway for hackers to intercept 2FA. The most suitable method is to keep going through the 2FA process every time you sign in. It’s up to you to decide what is best.
Use an alphanumeric password to unlock your phone
It’s so easy to set a 4 or 6-digit code that you have to enter every time you unlock your phone. This makes it easy for a hacker with the know-how to use password cracking technology to guess all the different number combinations.
Strengthen your phone by using an alphanumeric password which includes letters and numbers. Ideally, you want to add special characters such as ^ or £ to make it more difficult for a hacker to crack your password. Here is an example of an alphanumeric password.
^Br1de534£
Use a VPN if you are using public WIFI or avoid it altogether
There is always a temptation to connect to a public WIFI signal at locations such as an airport or cafe. Think twice before you do this! You are sharing that public WIFI connection with a lot of other users.
Many public WIFI connections are unsecured and do not require identity authentication and you never know who else is using it. Unsecured WIFI is typically marked without a padlock symbol on your mobile device.
Clever hackers can compromise public WIFI signals and record all the information you send across the internet such as passwords, emails and social media posts whilst you are connected. Worse yet, they can install malware on your device. This means they can even access your information after you have finished using the public WIFI.
The best advice when it comes to public WIFI is don’t use it altogether and this is a free option. If you really depend on public WIFI then use a Virtual Private Network (VPN), however, this will cost you.
These tools create an ‘encryption tunnel’ between your device and the VPN provider’s server. This means when you send data across the internet, it is encrypted when travelling between your device and the VPN server before reaching the final destination. Here is a simple visual explaining how this works.
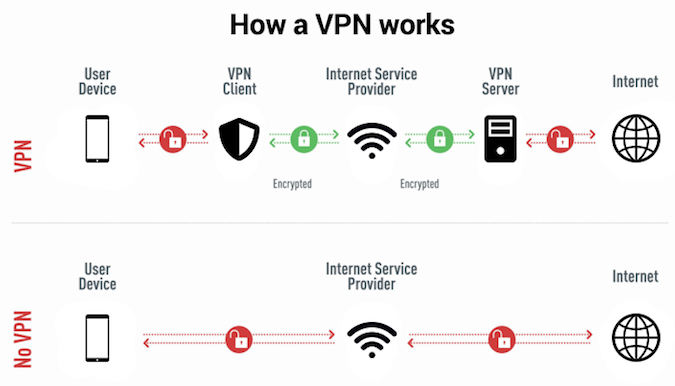
A VPN essentially adds a strengthened layer of encryption when you are using the internet. As a result, it’s extremely difficult for hackers to see what data you are transferring. This is why you should definitely use a VPN if you must access public WIFI. A comparison of different VPN providers is available here.
Don’t use a free VPN. If they are not making money from subscriptions, they are most likely generating income in other ways such as selling your data.
Use anti-virus software and scan regularly
Anti-virus software is specifically designed to protect your devices against malicious programs called malware which is commonly used by hackers. Viruses are a type of malware.
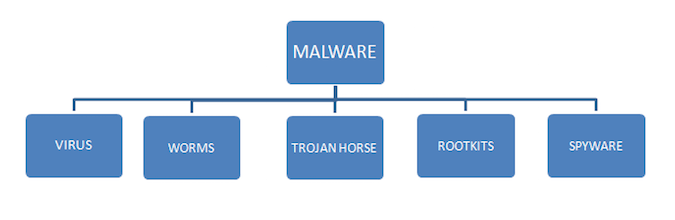
So anti-virus software essentially protects against most types of malware including viruses.
Chances are you are using anti-virus software. If you aren’t then I recommend you start using one. There are plenty of free providers. Here is an article that recommends the best paid and free antivirus software.
Ensure your anti-virus is always kept up to date. Some software providers include an automatic update option and the ability to schedule scans of your devices.
If you can’t schedule scans, it’s important that you are regularly scanning to check if any malware has been installed on your devices without your immediate knowledge.
For all you Mac users out there, please do not believe the myth that OS X is incapable of being infected by malware. It’s simply not true and you should always use appropriate anti-virus software.
Need insurance for your wedding & event business?
We provide bespoke cover packages for a wide range of professions.
Get a Quote
Lockdown your social media accounts
Be very careful about what information you share on social media sites. Remember, public information can easily be used by hackers to impersonate you and perform malicious activities. For example, mentioning what internet or telephone providers you use online could be used by malicious actors. They may impersonate you in an attempt to reset your passwords or find out more information.
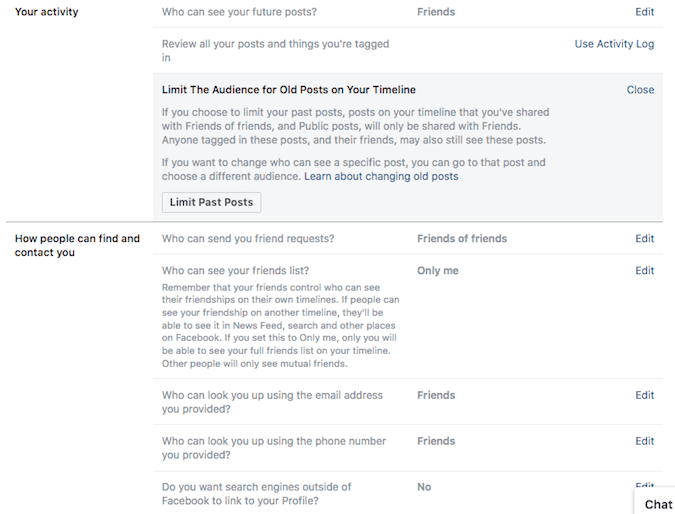
If you are not using your social media accounts for businesses purposes, consider taking advantage of the privacy settings provided by sites like Facebook. These settings are designed to keep your information out of public view.
For example, here are my Facebook profile settings. I definitely would recommend using the ‘Limit Past Posts’ option. Remember your Facebook profile pics and cover photos are always publicly available. Make sure you delete all photos you don’t want anyone else to see.
Google your personal information and remove results
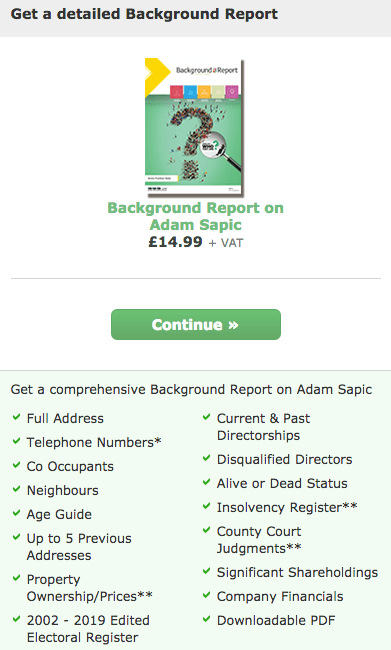
You’d be surprised what personal information about you is easily accessible online following a Google search using your name or email address. One really annoying example is 192.com – this site crawls public databases such as Companies House.
The site may also display your personal address which it got from the electoral register! I was really furious when I discovered this happened to me! These sites then sell your data. Another site that lists your info is locatefamily.com
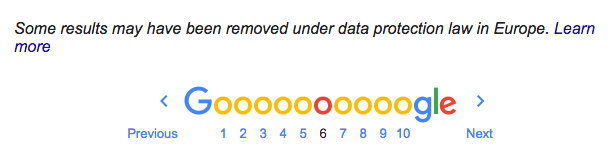
Luckily, you can request a record removal from 192.com and you can opt out of the open electoral register. Don’t forget to register to the Telephone Preference Service to minimise annoying marketing calls. My 192.com personal info was removed thanks to GDPR.
Ensure your website is regularly backed up
This goes without saying. If your website suffers a breach or cyber attack, you will most likely need to restore it using a backup copy. Your hosting provider may include this service as part of your package or at an additional cost.
If you are using WordPress, there are different plugins available. Some are free, others have a premium version. Not having a backup will only prolong your recovery time following an attack.
Do not click any links in suspicious emails or messages
This is called phishing and involves a hacker posing as a legitimate entity such as a company or public organisation. Phishing is usually carried out by email, text or through social media sites. The messages typically contain links leading to malicious sites designed to capture your personal information or install malware on your device. Here’s an example I received recently. When hovering my mouse over the website link, look at the URL highlighted at the bottom. Dodgy!
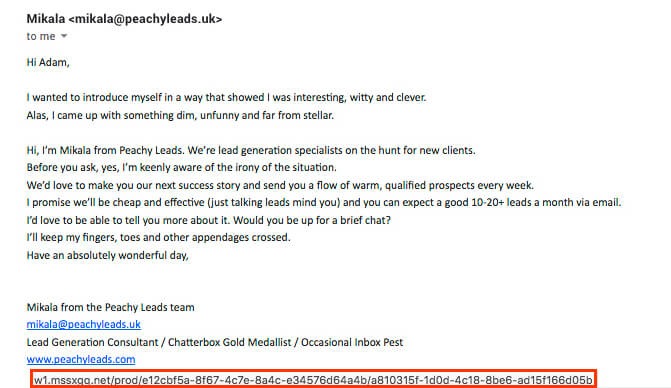
What’s worse is that phishing messages can look very similar to actual providers. Here is an example attempting to look like Paypal. If you hover your mouse over the ‘Confirm Now’ button, you can see the destination URL (highlighted in red at the bottom).
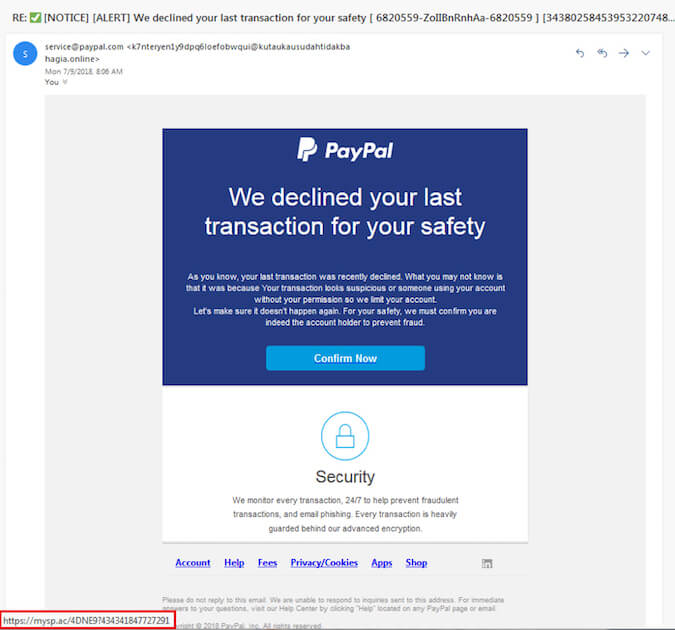
Remember these golden rules to avoid falling victim to phishing.
- Never open emails, respond to messages, friend requests or answer calls from people or numbers you do not recognise. Report senders as spam using your email system or block their numbers on your phone or their accounts on social media.
- Are you unsure about the legitimacy of a message because it looks like something you use such as Paypal or your bank? Contact them via telephone to verify whether the message is genuine. A lot of financial service providers contain information about what their communications look like on their websites.
- If it sounds too good to be true, it probably is. If you get that gut feeling that something is not right don’t take any further action. Be vigilant! It only takes one slip to fall.
You can take an online quiz which will test your knowledge about phishing by Take Five. It’s a national campaign that offers impartial advice to help everyone protect themselves from preventable financial fraud.
Use credit cards for online purchases
Under Section 75 of the 1974 Consumer Credit Act, credit cards must provide protection for purchases above £100 and below £30,000. Also, if you use your credit card to pay a deposit with the remaining amount paid using another method, your credit card provider could cover the whole amount. It’s best to confirm your protection rights with the card provider before taking out the credit card.
This protection is not offered on debit cards. Third party payment providers like Paypal have their own payment protection schemes so it’s important you understand them before using the provider.
Get cyber and data risks insurance
The Wedding Insurance Group provides this additional insurance product which comprehensively covers your computers systems and data whether it be online or offline. Our cyber and data risk policies have varying levels of cover depending on the size of your business, your dependence on computer systems and the amount and type of confidential or personal data you hold.
This type of insurance is specifically designed to cover your business losses arising from cyber or data incidents up to the limit of indemnity stated on your policy. You are also covered if a third-party claim is made against your business arising from your cyber or data liability. This also covers your legal defence costs. Better yet, our cyber insurance includes free crisis containment cover. This gives your business access to specialist PR support if a claim is likely to damage the reputation of your business.
Cyber and data risk insurance require your business to implement security measures, some of which have been covered in this article. In a nutshell, you can’t take out the insurance and carry on without strengthening basic security weaknesses. As with all insurance, there are terms and conditions so it’s best to contact us if you would like to know more.
Concluding thoughts
The main theme here is security vs convenience. Unfortunately, increasing your security online consumes time. However, as the old saying goes “It’s easy to be wise after the event”. A lot of hard work goes into building a wedding business. It would be such a shame for it all to come tumbling down due to a security weakness that could have been plugged.
Remember, it’s impossible to be hacker-proof. However, as we have explored in this article, there are some simple ways you can add extra layers of security to minimise the risk of a breach or cyber attack.